Hardware Engineering
What is social engineering in the context of cybersecurity ?
Social engineering refers to the psychological manipulation of individuals or groups into divulging confidential information. This tactic is often employed by cybercriminals to gain access to sensitive data, systems, or networks without being detected. In the context of cybersecurity, social engineering is a significant threat that exploits human behavior rather than technical vulnerabilities. There are several types of social engineering attacks, including phishing attacks, pretexting, baiting, quid pro quo attacks, tailgating or piggybacking, vishing (voice phishing), and smishing (SMS phishing). To protect against social engineering attacks, organizations can implement education and awareness programs, policies and procedures, technology tools, and an incident response plan. By understanding the various types of social engineering attacks and implementing appropriate countermeasures, organizations can significantly reduce their risk of falling victim to these deceptive tactics.

How does social engineering pose a risk to communication security ?
The Risks of Social Engineering to Communication Security discusses the dangers of social engineering, a form of manipulation that tricks people into sharing confidential information. Social engineering is a significant threat to communication security because it can infiltrate trusted environments, manipulate human emotions, be difficult to detect, use a variety of attack vectors, lead to data breaches, and lack awareness and training. To protect against social engineering attacks, organizations must implement comprehensive security awareness programs, establish strict verification procedures for sensitive requests, and create a culture of security where employees are encouraged to report suspicious activities without fear of reprimand.

How do I know if my iPhone needs a software update or a hardware repair ?
The text is a guide that helps iPhone users determine whether their device requires a software update or hardware repair. It outlines steps to check for available updates, restart the device, and reset it to factory settings if needed. The guide also suggests inspecting the iPhone for physical damage, testing basic functions, and checking battery health as indicators of potential hardware issues. If unsure about the cause, the text advises visiting an Apple Store or authorized service provider for further diagnostics.

Do I need new hardware to use Wi-Fi 6, or can I upgrade just my router ?
The article discusses the compatibility of Wi-Fi 6 with existing devices and whether an upgrade to a new router or new hardware is necessary. It explains that while older devices can still connect to a Wi-Fi 6 router, they will not fully utilize its benefits. Upgrading just the router allows all devices to connect using the latest technology, but for optimal performance, it's recommended to have devices that also support Wi-Fi 6. The article outlines the benefits of upgrading both the router and devices, such as increased speed, improved performance in crowded areas, and enhanced battery life. It also suggests considering factors like compatibility, cost, and future-proofing before making an upgrade decision.

Is geoengineering a viable solution to global warming ?
Geoengineering, also known as climate engineering or earth system management, refers to the intentional manipulation of the global climate on a large scale to counteract the effects of global warming and reduce the risks associated with climate change. While geoengineering has potential benefits such as mitigating climate change, providing faster responses compared to conventional methods, and being relatively inexpensive, it also comes with uncertainties regarding long-term effects, lack of international regulation and governance, and limited scope compared to other mitigation strategies. Therefore, geoengineering should not be seen as a substitute for conventional mitigation strategies but rather complement them. Extensive research and international cooperation are essential before implementing any large-scale geoengineering projects to ensure their safety and effectiveness in addressing climate change challenges.

What are the potential risks and drawbacks of geoengineering ?
Geoengineering, also known as climate engineering, refers to the deliberate large-scale manipulation of the Earth's climate system to counteract the effects of global warming. While it is still a theoretical concept, there are potential risks and drawbacks associated with its implementation. One of the biggest concerns about geoengineering is that it may have unintended consequences that could be worse than the problem it was intended to solve. For example, injecting sulphate aerosols into the stratosphere to reflect sunlight back into space could potentially deplete the ozone layer, leading to increased exposure to harmful UV radiation. Another risk is that some forms of geoengineering may have irreversible effects on the environment. Once implemented, it may be difficult or impossible to reverse the changes made, even if the original goal was achieved. This could lead to long-term damage to ecosystems and biodiversity. Geoengineering raises important ethical questions about who has the right to make decisions about manipulating the planet's climate. There are concerns that wealthy nations might use geoengineering to protect their own interests at the expense of poorer countries that are more vulnerable to climate change impacts. If something goes wrong with a geoengineering project, who would be held accountable? Determining liability for any negative consequences of geoengineering would be complex and controversial, especially if multiple parties were involved in its development and implementation. Some proposed geoengineering techniques may not be scalable enough to have a significant impact on global temperatures. For instance, ocean fertilization, which involves adding iron or other nutrients to stimulate plankton growth and enhance carbon uptake by oceans, may only work in certain regions and not be effective globally. Implementing large-scale geoengineering projects would require significant financial resources and ongoing maintenance. The cost-effectiveness and sustainability of such projects over the long term are unknown and could prove prohibitive for many countries. The public perception of geoengineering is likely to vary widely depending on cultural, religious, and political beliefs. Some people may view it as a "quick fix" for climate change while others may see it as an unnatural interference with nature. This could lead to social conflict and opposition to its implementation. Given the global nature of climate change, any attempt at geoengineering would require international cooperation and coordination. However, reaching consensus among diverse nations with different priorities and interests could prove challenging and time-consuming.
Can data encryption prevent data breaches and cyber attacks ?
Data encryption is a crucial security measure that can significantly reduce the risk of data breaches and cyber attacks by converting plain text into an unreadable format. However, it does not completely eliminate the risk of data breaches and cyber attacks. Encryption works through complex algorithms to scramble data so that it appears as random characters, requiring a secret key (or password) to decrypt the data back into its original form. There are two main types of encryption: symmetric and asymmetric. While encryption offers benefits such as confidentiality, integrity, authentication, and non-repudiation, it also has limitations including key management challenges, performance overhead, compatibility issues, human error, and advanced persistent threats (APTs). Therefore, organizations should implement other security measures such as firewalls, intrusion detection systems, regular security audits, and employee training programs to minimize the risk of cyber threats.
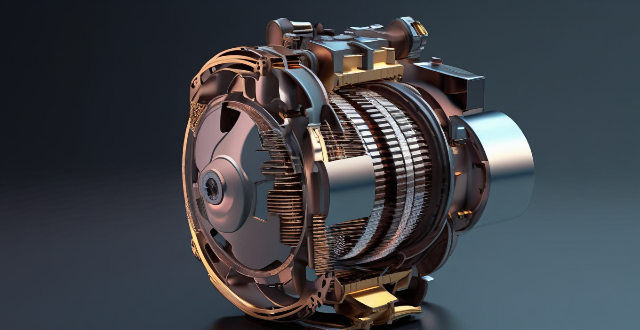
What are the advantages and disadvantages of using a combination motor drive compared to a single motor drive ?
The combination motor drive has several advantages over a single motor drive, including improved performance, enhanced reliability, flexibility in design, energy efficiency, and modularity and scalability. However, it also has disadvantages such as complexity, cost, space requirements, synchronization issues, and integration challenges.