Network Setting

What is the cost involved in expanding a network ?
Expanding a network involves costs in hardware, software, labor and other areas.

What are the best practices for setting a personal budget ?
The article outlines best practices for setting a personal budget to achieve financial stability and success. It suggests determining income, listing expenses, setting financial goals, creating a budget plan, tracking spending, and adjusting the budget as needed.
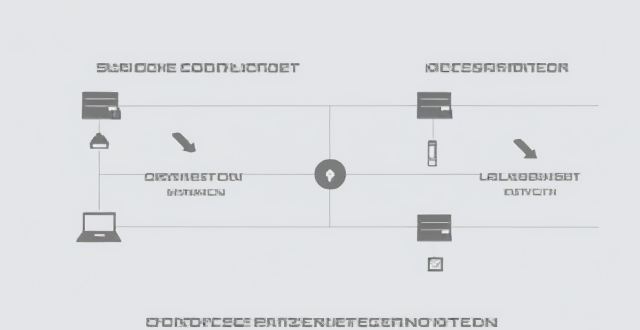
What is the difference between a router and a modem in network connectivity ?
The text delineates the differences between a router and a modem, highlighting their distinct roles within a network. A modem primarily converts digital signals to analog for transmission over telephone lines or cables, while a router creates a local area network (LAN) that enables multiple devices to connect and communicate with each other and the internet. Combination devices that integrate both functionalities are also discussed, noting their convenience but potential lack of advanced features compared to separate units. Understanding these differences is crucial for setting up and maintaining a reliable internet connection.
How can I reduce network latency in my home ?
To reduce network latency in your home, check your internet speed, upgrade your router, use wired connections, optimize router settings, limit bandwidth hogs, place your router strategically, use a Wi-Fi extender or mesh network, and close unused applications and tabs.

How does network expansion affect the overall network performance ?
Network expansion can significantly impact overall performance, offering benefits such as increased bandwidth, improved redundancy, and enhanced connectivity. However, challenges like compatibility issues, security concerns, and complexity management must be addressed to maintain optimal performance. Careful planning is crucial for successful network expansion.

How does network slicing differ from traditional network management techniques ?
Network slicing, enabled by SDN and NFV, allows creating multiple virtual networks on a common infrastructure for tailored services like IoT and automotive systems. It offers dynamic resource allocation, scalability, better security, and can simplify management through automation. In contrast, traditional network management is monolithic with static resources, complex and potentially less secure. Network slicing is a more adaptable solution for diverse and growing connectivity needs.

Is 5G network more secure than 4G ?
The question of whether 5G is more secure than 4G has been a topic of discussion among tech enthusiasts and security experts. While it's true that 5G brings many improvements over its predecessor, including faster speeds and lower latency, the question of security is complex and multifaceted. Let's dive into some key aspects to consider: ## Encryption and Authentication ### Key Points: - **Stronger Encryption**: 5G uses more advanced encryption methods compared to 4G. - **Enhanced Authentication Procedures**: 5G introduces new authentication mechanisms. #### Explanation: 5G networks employ stronger encryption standards than 4G. For instance, it uses algorithms like AES-256 for confidentiality, which is considered very secure. Moreover, 5G includes enhanced authentication procedures such as network function protection and improved identity privacy features. These enhancements make it harder for attackers to intercept or spoof user data. ## Network Slicing and Isolation ### Key Points: - **Network Slicing**: Allows multiple virtual networks on a shared physical infrastructure. - **Improved Isolation**: Helps in containing potential security breaches. #### Explanation: One of the innovative features of 5G is network slicing, which enables operators to create multiple virtual networks tailored for different services or customers. This can improve security by isolating sensitive communications from general traffic, reducing the risk of cross-contamination if one slice gets compromised. ## IoT and Device Density ### Key Points: - **Increased Connectivity**: 5G is designed to support a much higher number of devices. - **Potential Vulnerabilities**: More connected devices could mean more entry points for attacks. #### Explanation: With the rise of IoT (Internet of Things), 5G is expected to connect many more devices than 4G. While this opens up opportunities for smart cities, autonomous vehicles, etc., it also increases the potential attack surface. Each device could be a vulnerability that hackers might exploit. ## Security Standards and Regulations ### Key Points: - **Evolving Standards**: 5G security standards are still evolving. - **International Cooperation**: Global cooperation is essential for setting uniform security regulations. #### Explanation: As with any new technology, the security standards for 5G are still being developed and refined. There's an ongoing effort from international bodies to ensure that 5G networks worldwide adhere to stringent security guidelines. However, the effectiveness of these measures will depend on how consistently they are implemented and enforced across different countries and providers. ## Conclusion In conclusion, while 5G brings several improvements that can enhance security—such as stronger encryption and better authentication mechanisms—it also introduces new challenges due to increased connectivity and the need for global cooperation on security standards. Therefore, it's not straightforward to declare that 5G is inherently more secure than 4G without considering various factors and ongoing developments in both technologies.

What are the benefits of setting goals for studying and how do they impact motivation ?
The benefits of setting goals for studying include increased clarity and direction, improved motivation through short-term milestones and visual progress tracking, better time management with efficient planning and reduced procrastination, enhanced performance via targeted learning and a feedback loop, and stress reduction due to predictability and a sense of control. These advantages collectively contribute to heightened motivation, both immediately and in the long term, making goal setting an essential strategy for effective and enjoyable learning.

How do compression algorithms contribute to network optimization ?
Compression algorithms are crucial for network optimization by reducing data transmission, thus improving speed, bandwidth consumption, and network performance. They also enhance security and disaster recovery capabilities.

What are the best strategies for setting achievable learning goals ?
The text provides strategies for setting achievable learning goals, which include starting with a clear objective, breaking the goal into smaller steps, setting realistic timelines, tracking progress, and being flexible and open to change. The purpose of these strategies is to help individuals stay focused, motivated, and on track in their learning journeys.

What causes network latency ?
Network latency is a critical metric in networking, referring to the delay that data experiences when traveling between two points in a network. Understanding the causes of network latency is essential for optimizing productivity, collaboration, and user experience in today's digitally reliant world. The article delves into the various factors contributing to network latency and why it matters.

What factors affect wireless network coverage ?
**Wireless network coverage is influenced by multiple factors that include physical obstructions, distance from the access point, interference from other devices, environmental conditions, network infrastructure, device capabilities, regulatory limitations, and security settings.**

Can network expansion solve issues related to network congestion ?
## Topic Summary: Network Expansion as a Solution to Network Congestion Network congestion is a common problem that affects the performance of networks, leading to delays and reduced efficiency. One potential solution to this issue is network expansion, which involves increasing the capacity of the existing infrastructure by adding more hardware or upgrading existing equipment. This approach can alleviate network congestion by providing additional bandwidth for data transmission, improving overall performance, and reducing latency. However, network expansion also has its drawbacks, including high costs and the need for careful planning and implementation. Additionally, addressing the underlying causes of congestion is crucial for long-term success.
What are the benefits of using network slicing for businesses ?
Network slicing technology allows businesses to create multiple virtual networks on a shared physical infrastructure, offering benefits such as improved performance, cost efficiency, enhanced security, faster time-to-market, and increased innovation potential.

What is the role of a network hub in a computer network ?
In this text, the role of a network hub in a computer network is discussed. The main functions of a network hub are data transmission, connectivity, and collision domain management. However, the device also has limitations such as bandwidth sharing, security risks, and scalability issues. Despite its importance in connecting devices and allowing resource sharing, more advanced networking devices are often used in larger and more complex networks to overcome these limitations.

How do I optimize my network connection device for video conferencing ?
Optimizing your network connection device for video conferencing is essential for a smooth and reliable communication experience. Here are some steps to follow: 1. Check Your Internet Speed: Test your connection speed and upgrade your plan if necessary. 2. Choose the Right Hardware: Use a wired Ethernet connection if possible, and ensure that your router and modem are up-to-date. 3. Optimize Your Network Settings: Set up Quality of Service (QoS) on your router and keep its firmware updated. 4. Minimize Interference: Reduce wireless interference and limit bandwidth usage during important video calls. 5. Use a Dedicated Network for Video Conferencing: Create a separate Virtual Private Network (VPN) or invest in business-grade networking solutions. By following these steps, you can optimize your network connection device for video conferencing, ensuring smooth and reliable communication with colleagues and clients around the world.
What is the role of bandwidth management in network optimization ?
Bandwidth management is a critical component of network optimization, as it involves controlling and managing the amount of data that can be transmitted over a network at any given time. By effectively managing bandwidth, network administrators can ensure optimal performance and prevent congestion, leading to faster speeds and improved overall network efficiency. Key benefits of bandwidth management include improved network performance, reduced congestion, enhanced user experience, cost savings, and increased security. Techniques for effective bandwidth management include Quality of Service (QoS), traffic shaping, caching, compression, and load balancing. Best practices for bandwidth management involve monitoring network usage, implementing policies and guidelines, using QoS settings appropriately, updating hardware and software regularly, and educating users about proper network usage.
What technology is used to extend network coverage in remote locations ?
In remote locations, several technologies are used to extend network coverage, including satellite internet, wireless broadband (Wi-Fi), cellular data, long-range radio networks (LoRaWAN), and fiber optic cables. The choice of technology depends on factors such as cost, availability, and the specific needs of the users in those areas.