Network Connected

How can I stay connected with family and friends during an extended outdoor excursion ?
Staying connected with family and friends during an extended outdoor excursion is essential for maintaining relationships and ensuring safety. This guide explores various ways to stay connected, including planning ahead, using portable technology, establishing emergency plans, regular check-ins, leveraging social media and messaging apps, and sending physical mail. By following these tips, you can enjoy the great outdoors while staying connected with your loved ones.

How do I stay connected with family and friends back home while backpacking in Europe ?
Staying connected with family and friends while backpacking in Europe can be challenging. To maintain these connections, consider using technology wisely, setting up a communication schedule, sending postcards or letters, sharing your journey online, carrying portable power banks, being mindful of time zones, utilizing public phones and internet cafes, keeping it simple, storing important information safely, and embracing the disconnect. These tips will help you stay connected with loved ones without sacrificing the joys of traveling.

What is the role of a network hub in a computer network ?
In this text, the role of a network hub in a computer network is discussed. The main functions of a network hub are data transmission, connectivity, and collision domain management. However, the device also has limitations such as bandwidth sharing, security risks, and scalability issues. Despite its importance in connecting devices and allowing resource sharing, more advanced networking devices are often used in larger and more complex networks to overcome these limitations.

What are the best ways to stay connected and charged while traveling through the airport ?
Best Ways to Stay Connected and Charged at the Airport: Stay connected by using free Wi-Fi, downloading airline and airport apps for updates, and considering SIM cards or eSIMs for international travel. Stay charged by bringing a portable power bank, charging cables, an international travel adapter, and backup batteries. Take advantage of charging stations, priority lanes, and seat charging on planes.
Can you explain the function of a network switch in a home network setup ?
The article discusses the function of a network switch in a home network setup. The primary function of a network switch is to connect multiple devices together, either through Ethernet cables or wireless connections. It also manages data traffic within the network by forwarding data packets to their intended destination based on their IP address. Additionally, network switches enhance network performance by providing dedicated bandwidth to each connected device and prioritizing certain types of traffic over others. Finally, network switches come with various security features that help protect your home network from unauthorized access and cyber threats.

How does network slicing differ from traditional network management techniques ?
Network slicing, enabled by SDN and NFV, allows creating multiple virtual networks on a common infrastructure for tailored services like IoT and automotive systems. It offers dynamic resource allocation, scalability, better security, and can simplify management through automation. In contrast, traditional network management is monolithic with static resources, complex and potentially less secure. Network slicing is a more adaptable solution for diverse and growing connectivity needs.

How do I connect to a public Wi-Fi network ?
Connecting to a public Wi-Fi network is essential in today's digital age. Here are the steps: locate the Wi-Fi settings, select the network, connect to it, verify the connection, and troubleshoot if needed. Remember to use a VPN, limit sensitive activities, and keep software updated for security reasons.
What technology is used to extend network coverage in remote locations ?
In remote locations, several technologies are used to extend network coverage, including satellite internet, wireless broadband (Wi-Fi), cellular data, long-range radio networks (LoRaWAN), and fiber optic cables. The choice of technology depends on factors such as cost, availability, and the specific needs of the users in those areas.
What are the risks of connecting to a public Wi-Fi network ?
Connecting to a public Wi-Fi network can expose your device and personal information to various risks, including man-in-the-middle attacks, malware distribution, unauthorized access to your device, snooping and data theft, and social engineering attacks. To mitigate these risks, it is recommended to use a Virtual Private Network (VPN) to encrypt your internet traffic, keep your operating system and antivirus software up-to-date, enable your firewall, use websites with HTTPS encryption, verify the authenticity of the Wi-Fi network before connecting, and be cautious about which websites you visit and what information you enter while connected to public Wi-Fi.

What is the importance of having a good network coverage ?
The text discusses the importance of having a good network coverage in today's world where communication and connectivity are essential aspects of our daily lives. It outlines several reasons why having a strong and reliable network coverage is crucial, including improved communication, better access to information, enhanced productivity, entertainment on the go, safety and security, and business growth and opportunities. The text concludes that having a good network coverage is an integral part of our modern lifestyle and should not be overlooked when choosing a service provider or planning internet usage.

What steps can I take to secure my home network ?
Securing your home network is crucial in today's digital age where cyber threats are constantly evolving. Here are some steps you can take to ensure the safety and privacy of your home network: Change default router settings, use strong encryption, set up a guest network, update device software, use firewall and encrypt data, secure your wireless signal, control device access, and monitor network activity. By following these steps, you can significantly enhance the security of your home network and protect your personal information from potential cyber threats.

How can I protect my network from malware and viruses ?
Malware and viruses can cause significant damage to your network, including data loss, system crashes, and identity theft. To protect your network from these threats, you need to implement a comprehensive security strategy that includes installing antivirus and anti-malware software, using a firewall, keeping your system up-to-date, using strong passwords and 2FA, educating yourself and your employees, and regularly backing up your data. By implementing these steps, you can significantly reduce the risk of malware and virus infections on your network.

How can I improve my home's Wi-Fi network coverage ?
The text provides tips on how to improve Wi-Fi network coverage at home, including upgrading the router, changing its location, using extenders or mesh networks, updating firmware, adjusting settings, limiting bandwidth-heavy activities, replacing old devices, and using wired connections where possible.
What industries will benefit the most from network slicing capabilities ?
The article discusses the concept of network slicing, a technology derived from software-defined networking (SDN) and network function virtualization (NFV), which allows the partitioning of physical networks into multiple virtual networks to optimize resource allocation according to specific service requirements. It outlines the key benefits and applications of network slicing in various sectors such as automotive, healthcare, manufacturing, energy, financial services, and entertainment and media. The conclusion highlights the potential of network slicing to revolutionize communication systems and enhance service delivery, operational efficiency, and user experience across different industries.
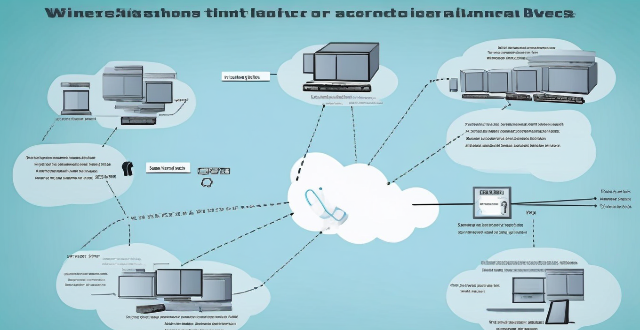
What strategies can be implemented to optimize wireless network connectivity ?
Optimizing wireless network connectivity is crucial for seamless internet access. Strategies include choosing the right location for the router, updating firmware and drivers, changing the wireless channel, using quality hardware, implementing Quality of Service (QoS) settings, securing the network, and reducing interference from other devices and appliances. These steps can improve wireless network performance and ensure efficient internet access.

How can women build a strong network in the business community ?
In today's competitive business landscape, building a strong network is crucial for success. For women, it is especially important to cultivate relationships with peers, mentors, and industry leaders. This guide will provide strategies and tips on how women can build a strong network in the business community by attending industry events and conferences, joining professional organizations, utilizing social media, seeking mentorship, and being proactive in maintaining relationships.

What are the latest trends in network security protection ?
Network security is a crucial aspect of modern computing, and it's constantly evolving to keep up with new threats. Here are some of the latest trends in network security protection: - AI and ML are becoming increasingly popular for detecting and responding to cyber threats. - IoT devices have poor security features or lack them altogether, making them easy targets for hackers. - With more businesses moving to the cloud, ensuring data is secure is essential. - Threat intelligence involves collecting information about potential threats and using it to improve defenses. - The zero trust model assumes that no one should be trusted by default, including those within an organization's network.
Why does my network latency fluctuate throughout the day ?
The article explores various reasons for fluctuations in network latency, including network congestion due to high traffic volume, large file transfers, and server load; physical distance and infrastructure issues related to geographical location, network hardware, and ISP differences; and local network conditions such as wireless interference, multiple devices sharing bandwidth, and malware or viruses affecting performance. It suggests ways to minimize latency fluctuations, like upgrading equipment, optimizing Wi-Fi setup, scheduling large downloads during off-peak hours, using wired connections, and scanning for malware.

Is 5G network more secure than 4G ?
The question of whether 5G is more secure than 4G has been a topic of discussion among tech enthusiasts and security experts. While it's true that 5G brings many improvements over its predecessor, including faster speeds and lower latency, the question of security is complex and multifaceted. Let's dive into some key aspects to consider: ## Encryption and Authentication ### Key Points: - **Stronger Encryption**: 5G uses more advanced encryption methods compared to 4G. - **Enhanced Authentication Procedures**: 5G introduces new authentication mechanisms. #### Explanation: 5G networks employ stronger encryption standards than 4G. For instance, it uses algorithms like AES-256 for confidentiality, which is considered very secure. Moreover, 5G includes enhanced authentication procedures such as network function protection and improved identity privacy features. These enhancements make it harder for attackers to intercept or spoof user data. ## Network Slicing and Isolation ### Key Points: - **Network Slicing**: Allows multiple virtual networks on a shared physical infrastructure. - **Improved Isolation**: Helps in containing potential security breaches. #### Explanation: One of the innovative features of 5G is network slicing, which enables operators to create multiple virtual networks tailored for different services or customers. This can improve security by isolating sensitive communications from general traffic, reducing the risk of cross-contamination if one slice gets compromised. ## IoT and Device Density ### Key Points: - **Increased Connectivity**: 5G is designed to support a much higher number of devices. - **Potential Vulnerabilities**: More connected devices could mean more entry points for attacks. #### Explanation: With the rise of IoT (Internet of Things), 5G is expected to connect many more devices than 4G. While this opens up opportunities for smart cities, autonomous vehicles, etc., it also increases the potential attack surface. Each device could be a vulnerability that hackers might exploit. ## Security Standards and Regulations ### Key Points: - **Evolving Standards**: 5G security standards are still evolving. - **International Cooperation**: Global cooperation is essential for setting uniform security regulations. #### Explanation: As with any new technology, the security standards for 5G are still being developed and refined. There's an ongoing effort from international bodies to ensure that 5G networks worldwide adhere to stringent security guidelines. However, the effectiveness of these measures will depend on how consistently they are implemented and enforced across different countries and providers. ## Conclusion In conclusion, while 5G brings several improvements that can enhance security—such as stronger encryption and better authentication mechanisms—it also introduces new challenges due to increased connectivity and the need for global cooperation on security standards. Therefore, it's not straightforward to declare that 5G is inherently more secure than 4G without considering various factors and ongoing developments in both technologies.

What steps can women take to build a strong professional network ?
Building a strong professional network is crucial for career growth and advancement. For women, it can be especially important as they often face unique challenges in the workplace. Here are some steps that women can take to build a robust professional network: 1. Attend industry events and conferences. 2. Join professional organizations and associations. 3. Utilize social media and online platforms. 4. Find a mentor or sponsor. 5. Participate in training programs and workshops. 6. Volunteer for committees or boards. 7. Stay in touch with colleagues and alumni.

How do I troubleshoot a faulty network connection device ?
This text provides a step-by-step guide on how to troubleshoot a faulty network connection device. It starts by identifying the problem, checking physical connections, restarting the device, checking network settings, updating firmware, checking for interference, and finally contacting support if all else fails. The text emphasizes the importance of patience and perseverance in troubleshooting technical issues.

What are the benefits of using a 5G network ?
The advent of the 5G network has brought about significant changes in the way we use technology. It offers several benefits that were not possible with earlier networks. Here are some of the key advantages: 1. **Faster Speeds**: Compared to 4G, 5G can provide download and upload speeds that are up to 10 times faster. 2. **Lower Latency**: With 5G, the delay is reduced significantly, making real-time communication more efficient. 3. **Increased Capacity**: 5G networks can handle more devices and connections at the same time. 4. **Improved Reliability**: They use advanced signal processing techniques to ensure stable connections. 5. **New Use Cases**: 5G opens up opportunities for new applications like virtual reality and smart cities.