Using User

Can I use multiple user accounts on my Apple computer ?
Using multiple user accounts on an Apple computer allows for privacy, security, customization, and parental controls. To set up additional user accounts, open System Preferences, click on Users & Groups, unlock the preferences pane, add a new user account, customize it, and repeat for each additional user. Switching between accounts can be done through the Apple menu by selecting "Log Out" or "Switch User."

Can you explain some lesser-known tips and tricks for customizing the user interface and experience using hidden features in iOS ?
This article provides a summary of some lesser-known tips and tricks for customizing the user interface and experience using hidden features in iOS. It covers topics such as Accessibility Shortcut, Reduce Motion, Increase Contrast, Reduce Transparency, Customize Control Center, Use Siri with Third-Party Apps, Use Split View in Safari, and Use Keyboard Shortcuts. These hidden features can help users personalize their device and make it more accessible and efficient to use.

What is network latency and how does it impact user experience ?
Network latency is the delay in data transmission over a network, influenced by factors such as distance, congestion, and hardware limitations. It negatively impacts user experience in online gaming, video conferencing, streaming services, web browsing, and online shopping, leading to frustration and reduced engagement. Reducing latency through optimized network infrastructure can enhance user satisfaction.

What are the benefits of using hidden features in iOS ?
The text discusses the benefits of using hidden features in iOS, including enhanced user experience, increased efficiency, access to experimental features, troubleshooting and problem-solving, and advanced customization. However, it also warns that using these features should be done with caution as they may not work as intended or could potentially cause issues with the device if not used properly. It is recommended to research and understand the feature thoroughly before enabling or using it, and to back up important data before making any significant changes.
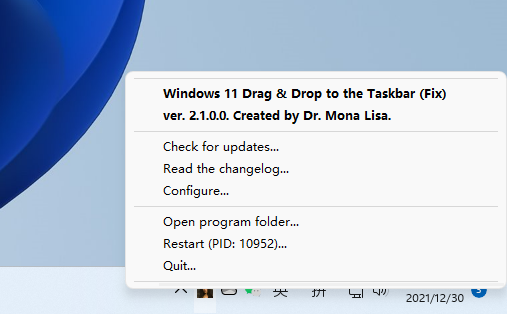
Win11 user ecstasy: the third-party gadget can realize the function of dragging and dropping to open files on the taskbar (with download)
How does two-factor authentication enhance security ?
Two-factor authentication (2FA) is a security process that requires two different factors to verify the user's identity, enhancing security by reducing the risk of unauthorized access, providing alerts for suspicious activities, protecting against various types of attacks, increasing user confidence in online services, and helping maintain compliance with security standards. Its implementation should be carefully planned considering both security requirements and user convenience.

What are some common security risks associated with using an iPhone ?
The article discusses common security risks associated with using an iPhone, including unauthorized access, malware attacks, phishing scams, and Wi-Fi networks. To protect against these risks, users should set strong passwords, enable two-factor authentication, avoid suspicious links and downloads, use a VPN when connecting to public Wi-Fi networks, and regularly scan their device for malware. By following these best practices, users can significantly reduce the risk of falling victim to security threats.

Are there any restrictions on what kinds of apps can be sold on the App Store ?
The App Store imposes restrictions on application content, developer behavior, sales and distribution, user experience, and more to maintain a high standard of quality and security for users. Developers must adhere to these guidelines to successfully sell their applications on the platform.

What are the risks associated with using public Wi-Fi networks ?
Using public Wi-Fi networks can expose you to various risks and vulnerabilities, including Man-in-the-Middle attacks, unencrypted data transmission, malware distribution, phishing scams, insufficient security measures, lack of privacy, session hijacking, and denial of service attacks. To protect yourself from these risks, it is essential to take precautions when using public Wi-Fi networks, such as using a virtual private network (VPN), avoiding sensitive activities like online banking or shopping, and keeping your device's software up-to-date with the latest security patches.

Can smart home gadgets learn user preferences and adapt accordingly ?
Smart home gadgets can learn user preferences and adapt accordingly through machine learning algorithms. Examples include personalized lighting, energy efficiency, security, entertainment, and voice assistants. These devices make our lives more convenient, comfortable, and efficient.

Can using a health management app reduce the risk of chronic diseases such as diabetes or heart disease ?
Health management apps can help reduce the risk of chronic diseases by monitoring health metrics, providing insights, promoting healthy habits, and issuing reminders. However, over-reliance, inaccuracies, and privacy concerns are downsides to consider. While beneficial, these apps should not replace professional medical advice.

What are the risks associated with using outdated software ?
Using outdated software poses risks including security vulnerabilities, compatibility issues, and limited functionality. Regular updates are crucial for maintaining security, compatibility, and access to new features.

How does the new product compare to its competitors ?
The new product distinguishes itself from competitors through innovative features, smart pricing, enhanced user experience, and precise market positioning. Key aspects include superior performance, a user-friendly interface, extensive customization options, seamless integration capabilities, an affordable entry level, tiered pricing model, value-added services, simplified navigation, responsive customer support, regular updates, niche specialization, brand storytelling, and community building.

Can I use Apple Pay internationally ?
Apple Pay is available in over 20 countries and regions worldwide, allowing users to make convenient and secure payments using their iPhone, Apple Watch, or iPad. To use Apple Pay internationally, users need to ensure their device supports it and set up a payment method accepted in the country they are visiting. Using Apple Pay offers benefits such as convenience, security, speed, and compatibility with popular apps and services around the world.

How do data protection regulations apply to social media platforms ?
This article discusses the crucial role of data protection regulations in safeguarding user information on social media platforms. It outlines key principles such as transparency, purpose limitation, and accountability that guide the handling of personal data by these platforms. The responsibilities of both social media platforms and users are highlighted, emphasizing the importance of informed consent, security measures, and user control. The article concludes by stressing the mutual responsibility of platforms and users in promoting a safe online environment through adherence to data protection regulations.

How can I stay safe while using mobile banking apps ?
The text provides a detailed guide on how to ensure the safety of personal and financial information while using mobile banking apps. It suggests downloading apps from official app stores, keeping them updated, setting up multi-factor authentication, using strong passwords, being cautious with public Wi-Fi, monitoring account regularly, not saving log-in details, and being wary of phishing scams. These measures can significantly enhance the security of mobile banking activities and protect financial information from potential threats.

What are the benefits of using the new product ?
Benefits of Using the New Product: - Improved Efficiency: Streamlined tasks, automation, integration with other tools, and a simplified interface save time and work more efficiently. - Enhanced Performance: Advanced technologies and algorithms enable faster and accurate processing, leading to improved productivity and higher quality outputs. - Customization Options: Extensive customization options allow users to tailor the product to their specific needs and preferences, creating a personalized experience. - Scalability and Flexibility: The product is designed to be scalable and flexible, making it suitable for both small businesses and large enterprises, and can accommodate growing demands and changing requirements.

Can I upgrade the storage capacity of my iPhone myself or do I need to go to an authorized service center ?
The storage capacity of an iPhone is a fixed component that cannot be upgraded by the user. Unlike some other devices, such as laptops or desktop computers, where you can add more storage by installing additional hard drives or solid-state drives (SSDs), iPhones do not have this capability. The storage chip in an iPhone is soldered onto the logic board and is not designed to be removed or replaced by the user. There are several reasons why you cannot upgrade your iPhone's storage: 1. Design and Manufacturing Choices: Apple designs its iPhones with a focus on thinness, durability, and water resistance. To achieve these goals, components are often tightly integrated and sealed within the device. This means that critical parts like the battery and storage are not meant to be user-serviceable. 2. Security and Reliability: By sealing the storage inside the device, Apple can ensure that it will function reliably over the lifespan of the device. Additionally, this approach helps maintain the security of the device, as tampering with internal components could potentially compromise the integrity of the iOS operating system. 3. Warranty and Support Considerations: If users were to attempt to upgrade their own storage, there is a high likelihood of damaging the device, which could void the warranty. Moreover, any issues that arise from unauthorized modifications might not be covered by Apple's support services. If you need more storage space, your best option is to purchase a new iPhone with the desired capacity. When buying, consider how much storage you will need in the long term to avoid finding yourself in the same situation again. You can also use cloud storage services like iCloud, Dropbox, or Google Drive to store photos, documents, and other data. This can help alleviate storage constraints on your device. Regularly review and manage the contents of your iPhone to free up space. Delete unused apps, offload unused data, optimize photos, and clear caches. Performing a backup and then restoring your iPhone can sometimes clear out hidden caches and other unnecessary data, giving you a bit more usable space. If all else fails, upgrading to a newer model with more built-in storage might be necessary.

What role does social media play in product review dissemination ?
The article discusses the significant role of social media in product review dissemination. It highlights the concept of "social proof" where people trust and adopt a product seeing others using it and sharing positive reviews. Social media platforms provide a platform for users to share their experiences with products, both good and bad, which can greatly influence potential customers' purchasing decisions. User-generated content (UGC) is a powerful tool for brands looking to promote their products. By encouraging customers to share their experiences with a product on social media, brands can leverage the power of social proof to attract new customers. Influencer marketing is another way that social media affects product review dissemination. Brands partner with influencers who have large followings on social media platforms to promote their products. Online reviews have become an essential part of the purchasing process for many consumers. Social media platforms provide a space for users to share their thoughts and opinions about products, allowing potential customers to make informed decisions before making a purchase. The trustworthiness, variety of opinions, and timeliness of online reviews greatly impact a consumer's decision to purchase a product or not. In conclusion, social media plays a crucial role in product review dissemination by providing a platform for users to share their experiences with products, promoting user-generated content and influencer marketing, and facilitating the sharing of online reviews.

How do I take stunning landscape photos using my iPhone ?
To take stunning landscape photos using your iPhone, focusTo take stunning landscape photos using your iPhone, focus the rule of thirds and play with perspectives, and mind details such as color palette and moment timing. Post-process with editing apps and accessories like a tripod or external lenses for improved results.

How can blockchain technology be used in voting systems to ensure transparency and fairness ?
Blockchain technology, known for its role in cryptocurrencies, can enhance voting systems by ensuring transparency, security, and fairness. It provides immutable record keeping, public verifiability, and a comprehensive audit trail. Blockchain also protects voters' identities, decentralizes the voting process, and automates vote counting. Implementing this technology requires designing the blockchain infrastructure, developing a user-friendly interface, testing, pilot programs, stakeholder education, and full implementation. However, challenges such as scalability, user adoption, legal and regulatory hurdles, and technical security must be addressed.

Can I use Apple Pay for online purchases ?
Apple Pay is a mobile payment and digital wallet service that allows users to make secure and convenient payments using their Apple devices. It works by transmitting payment information between the user's device and the merchant's payment terminal using near-field communication (NFC) technology. Using Apple Pay for online purchases offers several benefits, including convenience, security, speed, and integration with other Apple services. To set up Apple Pay for online purchases, users must add their credit or debit card details to the Wallet app on their iPhone or iPad, choose a default card, look for the Apple Pay button at checkout when shopping online, confirm their payment using Touch ID or Face ID, and wait for confirmation from the merchant. If issues arise while using Apple Pay for online purchases, users can check their device compatibility, update their billing and shipping information, or contact customer support for assistance.