Security Test

How often should I test my home security system to ensure it's working properly ?
Testing your home security system regularly is crucial for maintaining its effectiveness and ensuring that it functions as intended when you need it the most. Here are some guidelines on how often you should test various components of your home security system: - Alarms and Sensors: Monthly testing, check batteries every six months - Surveillance Cameras: Weekly check, review footage periodically - Keypads and Control Panels: Monthly verification, test backup power source every six months - Communication Systems: Quarterly testing, phone line check if using a landline - Environmental Sensors: Annually or seasonally testing, replace batteries annually Steps for testing your home security system include consulting your user manual, notifying authorities if connected to a monitoring service, performing visual inspections, testing each component according to recommended frequency, documenting results, and addressing any issues promptly. By following these guidelines and steps, you can ensure that your home security system remains reliable and effective in protecting your home and loved ones.
How often should I test my burglar alarm system ?
Test your burglar alarm system monthly to ensure it's functioning properly. Include sensors, detectors, backup power source, and monitoring center communication in the test. Annual maintenance should involve inspecting wiring, cleaning components, and updating software. Test again after home changes or if issues arise.

How can I manage test anxiety effectively ?
Test anxiety is a common issue among students that can be managed effectively through various strategies. Recognizing symptoms, practicing mindfulness, seeking support, preparing early, and staying healthy are some ways to combat test anxiety. Additionally, visualizing success, using relaxation techniques, setting realistic goals, staying organized, pacing oneself, and focusing on one question at a time can help improve performance. After the test, review mistakes without judgment, reflect on performance, and celebrate efforts regardless of the outcome.

Is there a way to completely eliminate test anxiety ?
Test anxiety is a common problem that affects many students. It can cause physical symptoms such as sweating, trembling, and rapid heartbeat, as well as mental symptoms such as difficulty concentrating and negative thoughts. While it may not be possible to completely eliminate test anxiety, there are several strategies that can help reduce its impact. Understanding Test Anxiety Test anxiety is the feeling of worry or fear that comes before or during an exam. It is a type of performance anxiety, which means it is related to how well you think you will do on the test. The more importance you place on the test, the more anxious you are likely to feel. Strategies for Reducing Test Anxiety Preparation is key to reducing test anxiety. Make sure you have studied thoroughly and understand the material. Create a study schedule and stick to it. This will help you feel more confident and prepared when the test day arrives. Positive thinking can also help reduce test anxiety. Try to replace negative thoughts with positive ones. For example, instead of thinking "I'm going to fail," try saying "I am prepared and I can do this." Visualize yourself succeeding on the test. Relaxation techniques such as deep breathing, meditation, or progressive muscle relaxation can help reduce anxiety. Practice these techniques regularly, not just on the day of the test. Time management is important for reducing test anxiety. Make sure you have enough time to complete the test. Don't wait until the last minute to start studying. Also, manage your time during the test by allocating a certain amount of time for each section. Maintaining a healthy lifestyle can also help reduce test anxiety. Get enough sleep, eat a balanced diet, and exercise regularly. Avoid caffeine and sugar, which can increase anxiety. If your test anxiety is severe, seek support from a counselor or therapist who specializes in anxiety disorders. They can provide additional coping strategies and treatments such as cognitive-behavioral therapy (CBT). Conclusion While it may not be possible to completely eliminate test anxiety, there are several strategies that can help reduce its impact. By understanding test anxiety, preparing thoroughly, practicing positive thinking and relaxation techniques, managing your time effectively, maintaining a healthy lifestyle, and seeking support if needed, you can minimize the effects of test anxiety and improve your performance on exams.
How can I distinguish between normal nervousness and excessive test anxiety ?
Normal nervousness is a natural response to stress, while excessive test anxiety can have negative effects on performance and well-being. Signs of excess test anxiety include excessive worry, avoidance behavior, physical symptoms, negative self-talk, and behavioral changes. Seeking help from a trusted source can provide guidance and support to manage anxiety and improve performance.

How can I integrate smart home devices with my home security system ?
The article provides a step-by-step guide for integrating smart home devices with a home security system, including determining compatibility, selecting the right devices, installing and configuring them, connecting to the security system, and testing the integration. The goal is to enhance safety and convenience by allowing remote control and monitoring of access, video surveillance, sensors, and lighting.

What techniques can help me stay calm during a test ?
Techniques to Stay Calm During a Test Staying calm during a test can greatly improve your performance. Here are some techniques that can help you stay focused and relaxed: 1. Deep Breathing: Take slow, deep breaths to slow down your heart rate and lower your blood pressure, reducing feelings of anxiety and stress. 2. Visualization: Picture yourself successfully completing the test and achieving your desired outcome, boosting your confidence and relaxation. 3. Positive Self-Talk: Replace negative thoughts with positive affirmations that boost your confidence and motivation. 4. Break Down the Test into Smaller Parts: Focus on one question at a time without worrying about the others. 5. Time Management: Allocate enough time for each section of the test and stick to your plan, working steadily but efficiently.

Are there any specific exercises for dealing with test anxiety ?
Managing Test Anxiety: Strategies for Success Test anxiety is a common issue faced by many students, especially during exams. It can have a negative impact on performance and overall well-being. However, there are specific exercises that can help in dealing with test anxiety. In this article, we will discuss some effective strategies for managing test anxiety. Mindfulness meditation is a powerful tool for reducing stress and anxiety. By focusing on the present moment and observing thoughts without judgment, you can learn to calm your mind and reduce feelings of anxiety. Deep breathing exercises can help to slow down your heart rate and relax your muscles, reducing feelings of anxiety. Visualization techniques involve imagining yourself successfully completing a task or achieving a goal. This can help to build confidence and reduce anxiety. Cognitive restructuring involves identifying and challenging negative thoughts that contribute to anxiety. By replacing these thoughts with more realistic and positive ones, you can reduce feelings of anxiety. In conclusion, test anxiety is a common issue faced by many students, but there are specific exercises that can help in dealing with it. Mindfulness meditation, deep breathing exercises, visualization techniques, and cognitive restructuring are all effective strategies for managing test anxiety. By practicing these exercises regularly, you can reduce feelings of anxiety and improve your performance on exams.

How can I monitor my home security system remotely ?
This guide provides a comprehensive overview of how to monitor your home security system remotely. It covers choosing a reliable security system, connecting it to the internet, monitoring your home remotely, and maintaining your security system. The guide emphasizes the importance of researching and selecting a suitable security system, establishing a secure internet connection, setting up remote access, viewing live streaming footage, receiving alerts and notifications, controlling your security system remotely, regular maintenance, and software updates. By following these steps, you can ensure the safety and security of your home while away.

What are the best practices for network security protection ?
The text provides a detailed outline on the best practices for network security protection, which can be summarized in the following points: 1. **Use Strong Passwords**: Create complex passwords using a mix of characters and numbers, change them regularly, avoid personal information, and use a password manager. 2. **Keep Software Up-to-date**: Regularly update all software to patch vulnerabilities and enable automatic updates where possible. 3. **Implement Firewall Protection**: Use both hardware and software firewalls, configure rules to allow necessary traffic only, and monitor firewall logs. 4. **Use Encryption**: Encrypt sensitive data in transit and at rest, use VPNs for remote connections, and implement end-to-end encryption for high-security communications. 5. **Educate Employees on Security Best Practices**: Conduct regular training, encourage safe online behavior, and establish clear policies for device and internet use. 6. **Limit Access Rights**: Grant access based on need, review and revoke unnecessary rights, and use multi-factor authentication for sensitive resources. 7. **Backup Data Regularly**: Create regular backups, test them periodically, and implement version control for important files. 8. **Monitor Network Activity**: Use IDS and IPS systems, set up alerts for unusual activity, and conduct regular security audits. By adhering to these practices, organizations can significantly enhance their network security posture and mitigate the risks associated with cyber threats.

In 3D graphics, mesh is a set of vertices, edges and faces that define the shape of an object. In the current drawing pipeline, all geometric data in the mesh must be processed sequentially before any other steps can be taken. This can be a major performance bottleneck.
The mesh shader replaces the old pattern with a new geometric processing method, which simplifies the graphics pipeline and provides developers with greater flexibility and control. Mesh shaders can process some segments of the mesh in parallel, called "mesh segments", with a greater degree of flexibility and control.

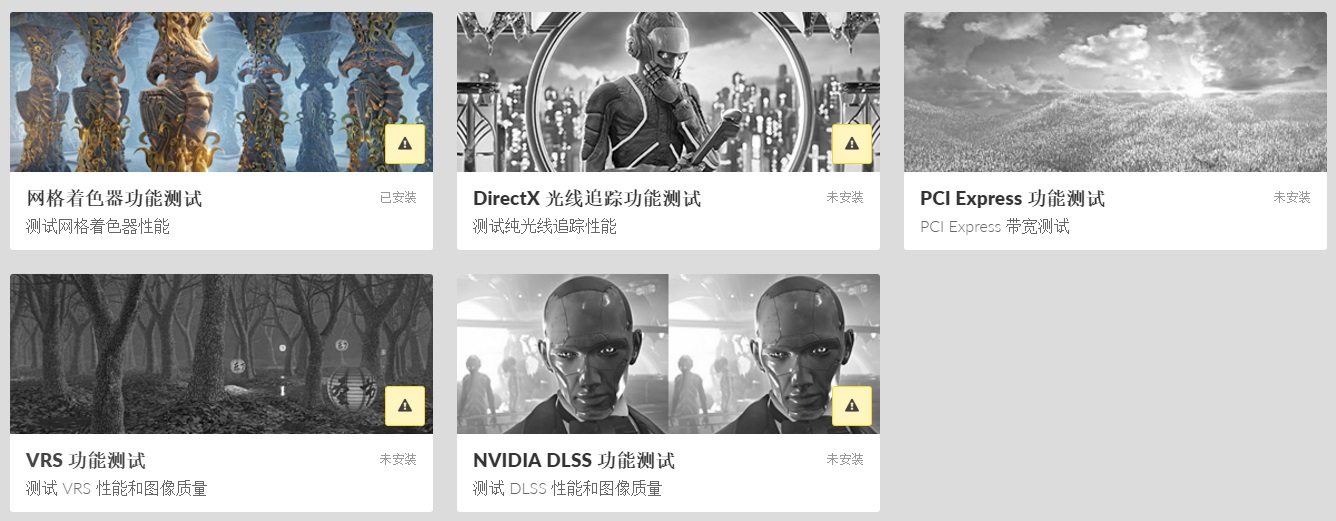
Users need to update 3dmark software to the latest version, and you can see this option in the "function test" area below the test list. In addition, there are DirectX ray tracing function test, PCI Express function test and so on.
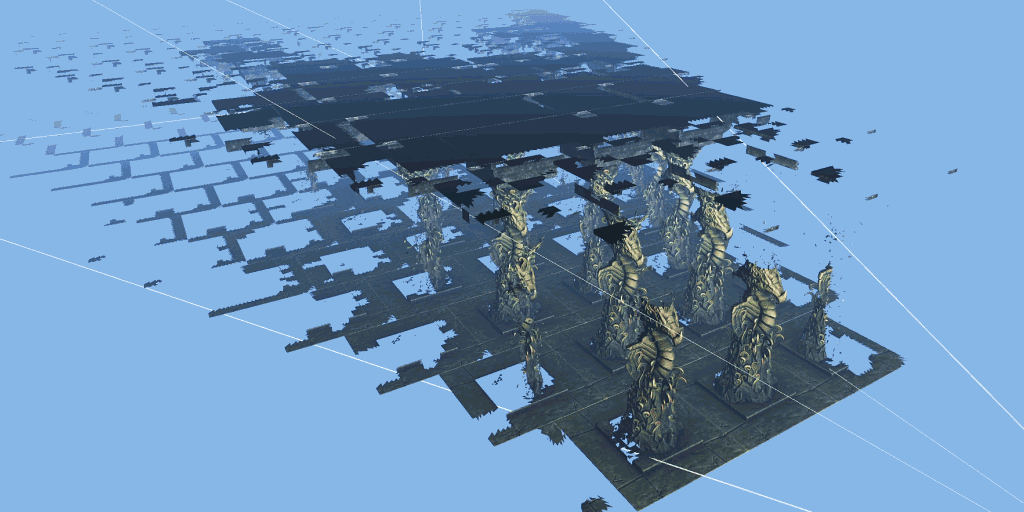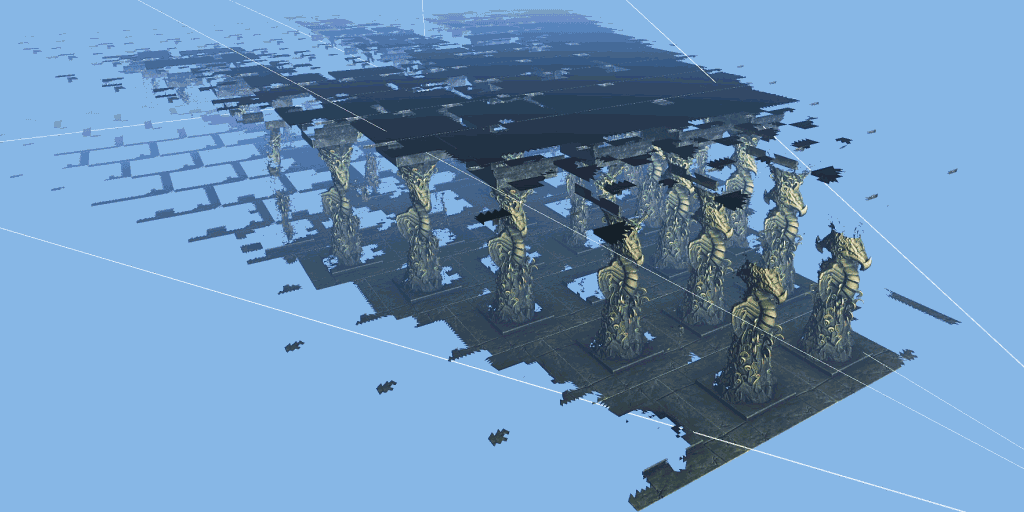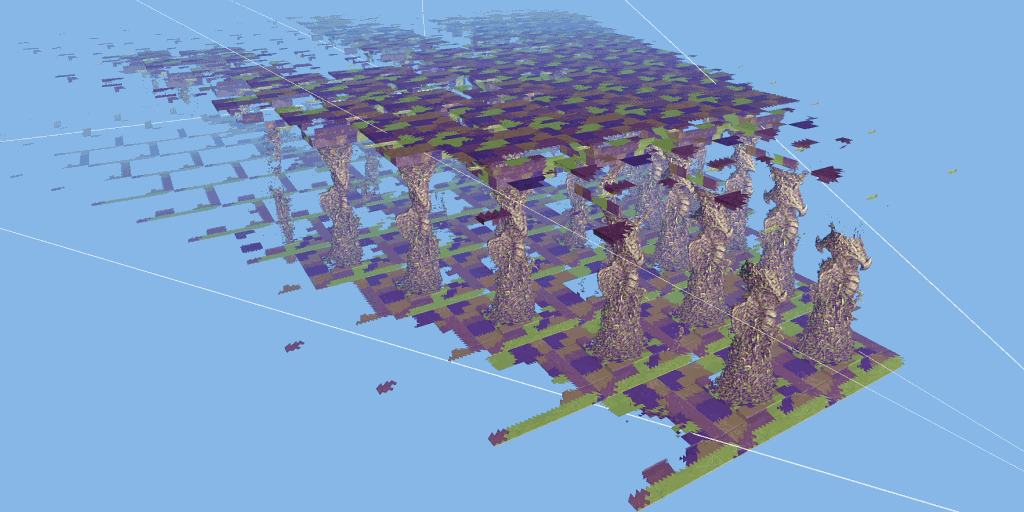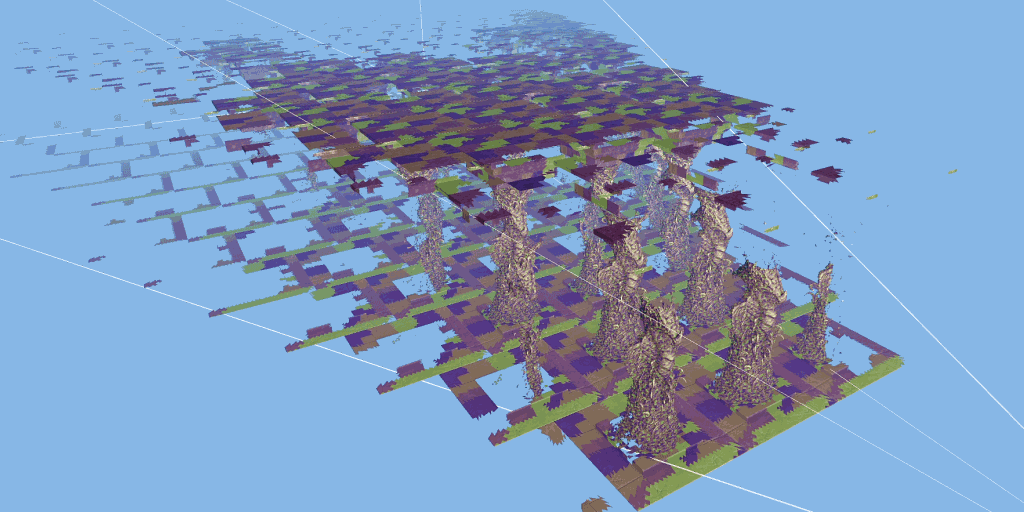
The 3dmark mesh shader function test will show you how the game engine can effectively eliminate the invisible geometry of the camera using the mesh shader pipeline, so as to improve the performance of the game.
The test scenario is a hall containing many rows of carved columns with high fineness. When the camera moves in the scene, the columns in the foreground block the scenery behind.
The 3dmark mesh shader function test includes an interactive mode that can help you intuitively see the benefits of using mesh shaders. You can pause and jump to different parts of the timeline and change settings in real time. Use the visualizer options to highlight mesh clips, or view the level of detail (LOD) used by each mesh clip.
Major update of 3dmark: the function test of mesh shader can be carried out, and dx12 ultimate needs to be supported
How does two-factor authentication enhance security ?
Two-factor authentication (2FA) is a security process that requires two different factors to verify the user's identity, enhancing security by reducing the risk of unauthorized access, providing alerts for suspicious activities, protecting against various types of attacks, increasing user confidence in online services, and helping maintain compliance with security standards. Its implementation should be carefully planned considering both security requirements and user convenience.

What are the security concerns related to Smart Grid Technology ?
Smart grid technology, which uses digital communication technologies to monitor and control the flow of electricity, offers benefits such as increased efficiency and reliability. However, there are security concerns that need to be addressed, including cyber attacks, data breaches, insider threats, physical security risks, and interdependencies with other critical infrastructures. It is essential to implement strong cybersecurity measures, strict access controls, and robust physical security protocols to protect the system's integrity and confidentiality.

What should I check before buying a second-hand iPhone ?
When purchasing a used iPhone, there are several factors to consider to ensure that you are getting a good deal and a functional device. Here are some important steps to take: 1. Check the Physical Condition - Examine the Screen for cracks, scratches, or damage. - Inspect the Body for major dents or scratches. - Test Buttons and Ports including volume buttons, power button, charging port, and headphone jack. 2. Verify the Functionality - Check Battery Health using a battery health app or asking the seller. - Test Camera Quality by taking photos/videos. - Speaker and Microphone Test by playing music/videos and making calls or recording voice memos. 3. Software and Security - iOS Version compatibility with latest apps and services. - Activation Lock removal from previous owner's Apple ID account. - iCloud logout and Find My Phone disablement to prevent remote locking or tracking issues. 4. Carrier Compatibility - Determine if the iPhone is locked to a specific carrier or unlocked for multiple networks. - SIM Card Slot condition and functionality. 5. Warranty and Return Policy - Inquire about any remaining manufacturer warranty or extended warranty purchased by the previous owner. - Clarify the return policy in case of problems after purchase that were not apparent during inspection.

What are the security concerns related to IoT ?
The article discusses the major security concerns related to the Internet of Things (IoT), such as data privacy and confidentiality, device security, network security, physical security, and software vulnerabilities. It emphasizes the need for implementing appropriate security measures to ensure the secure deployment of IoT devices and protect sensitive information from unauthorized access.

How do firewalls contribute to network security ?
Firewalls are crucial for network security, offeringFirewalls are crucial for network security, offering, blocking unwanted connections, preventing preventing network intrusion, enforcing security policies, providing VPN support, integrating with other security systems, protecting against known threats, offering customizable features, ensuring scalability and performance, and reducing the risk of data breach.

Can blockchain technology improve data security and privacy ?
Blockchain technology has been touted as a revolutionary tool that can improve data security and privacy. Its decentralized nature, encryption, and transparency make it difficult for attackers to compromise the network. Additionally, its anonymity, control over personal data, and smart contracts enhance privacy by giving individuals more control over their information.

How do remote education platforms ensure data privacy and security ?
Remote education platforms ensure data privacy and security through encryption, access controls, two-factor authentication, regular security audits, and data retention policies. These measures help protect user data during transmission and storage, restrict access to sensitive information, add an extra layer of security, identify and fix vulnerabilities, and minimize the risk of data breaches.

How does climate change affect food security and nutrition ?
Climate change significantly impacts global food security and nutrition by causing extreme weather events, altering ecosystems, reducing water availability, affecting marine life, posing agricultural challenges, and diminishing nutrient intake. Mitigation strategies include sustainable agriculture practices, dietary diversification, and research and development to ensure future food security and nutrition.

What are some tips for getting through security quickly and efficiently ?
Getting through security quickly and efficiently requires preparation and knowledge. Pack smart by following the 3-1-1 rule for liquids, keeping electronics separate, storing medications in their original containers, and wearing easy-to-remove shoes and jackets. Know the rules by researching specific security policies, having travel documents ready, and avoiding restricted items. At the security checkpoint, prepare your belongings by placing metal objects in your carry-on bag and separating liquids. Follow procedures by staying alert, complying with instructions, and moving swiftly. After security, reorganize and regroup by repacking liquids and reassembling any removed accessories or outer layers. Stay informed about any updates to security procedures before your next trip.

What are the latest trends in network security protection ?
Network security is a crucial aspect of modern computing, and it's constantly evolving to keep up with new threats. Here are some of the latest trends in network security protection: - AI and ML are becoming increasingly popular for detecting and responding to cyber threats. - IoT devices have poor security features or lack them altogether, making them easy targets for hackers. - With more businesses moving to the cloud, ensuring data is secure is essential. - Threat intelligence involves collecting information about potential threats and using it to improve defenses. - The zero trust model assumes that no one should be trusted by default, including those within an organization's network.

What are the main threats to communication security ?
The text discusses the main threats to communication security, which include eavesdropping and unauthorized access, malware and viruses, social engineering and phishing, insider threats, and DoS attacks. It also provides mitigation strategies for each threat, such as encryption, secure networks, physical security, antivirus software, firewalls, software updates, awareness training, email filters, multi-factor authentication, access controls, monitoring and auditing, termination procedures, rate limiting, content delivery networks (CDNs), and intrusion detection systems (IDS).

What are the potential impacts of climate conflicts on global security ?
Climate conflicts have the potential to significantly impact global security by causing economic disruption, political instability, and even armed conflict. Governments and international organizations must recognize this issue and take action to mitigate the effects of climate change.

What are some examples of how climate change has affected international security ?
Climate change has significant implications for international security, including resource scarcity and competition, displacement and migration, state fragility and failed states, environmental refugees, and national security threats. These challenges require global cooperation and strategic planning to mitigate their effects on international stability.

Does restrictive immigration policy improve national security ?
The text discusses the complex question of whether restrictive immigration policy enhances national security. It explores various aspects including economic impact, social cohesion, international relations, and internal security dynamics to provide a nuanced understanding. The text concludes that while a restrictive immigration policy might seem appealing from a national security standpoint, it is not a silver bullet, as benefits must be weighed against potential negative impacts on different factors. A balanced approach that ensures thorough vetting without undue restrictions might prove more effective in enhancing national security in the long term.

Can I retire early without jeopardizing my financial security ?
Retiring early is a goal for many, but it requires careful planning to ensure financial security. Key steps include assessing your current finances, setting clear retirement goals, creating a comprehensive plan, and seeking professional advice. By following these strategies, you can achieve early retirement without jeopardizing your financial well-being.